上一篇文章为window的openvpn连接方式
本次为linux的openvpn连接方式,其实都差不多只要在服务器把证书弄好就可以了
直接上操作,简化操作步骤,服务端的操作全为脚本
实验环境
| 公网ip | 内网ip | 服务类型 |
|---|---|---|
| 192.168.121.159 | 客户端 | |
| 192.168.121.160 | 192.168.122.253 | 服务端 |
首先需要配置好epel源,我是使用的是阿里云的epel源
wget -O /etc/yum.repos.d/epel.repo https://mirrors.aliyun.com/repo/epel-7.repo然后安装对应软件包,并执行相关配置操作
#! /bin/bashyum clean allyum makecache#然后安装openvpn和制作证书工具yum -y install openvpnyum -y install easy-rsayum -y install expect# 准备相关配置文件echo "生成服务器配置文件"cp /usr/share/doc/openvpn-2.4.12/sample/sample-config-files/server.conf /etc/openvpn/echo "准备证书签发相关文件"cp -r /usr/share/easy-rsa/ /etc/openvpn/easy-rsa-serverecho "准备签发证书相关变量的配置文件"cp /usr/share/doc/easy-rsa-3.0.8/vars.example /etc/openvpn/easy-rsa-server/3/varsecho "初始化服务端PKI生成PKI相关目录和文件"cd /etc/openvpn/easy-rsa-server/3./easyrsa init-pkiecho "创建CA证书"# ./easyrsa build-ca nopassexpect <<EOFspawn ./easyrsa build-ca nopassexpect { "Easy-RSA" {send "\n"}}expect eofEOFcat pki/serial echo "生成服务端证书"# ./easyrsa gen-req server nopassexpect <<EOFspawn ./easyrsa gen-req server nopass expect { "server" {send "\n"}}expect eofEOFecho "签发服务端证书"# ./easyrsa sign server serverexpect <<EOFspawn ./easyrsa sign server server expect { "*details:" {send "yes\n"}}expect eofEOFecho "创建 Diffie-Hellman 密钥"./easyrsa gen-dhcat > /etc/openvpn/server.conf <<EOFport 1194proto tcpdev tunca /etc/openvpn/certs/ca.crtcert /etc/openvpn/certs/server.crtkey /etc/openvpn/certs/server.key # This file should be kept secretdh /etc/openvpn/certs/dh.pemserver 10.8.0.0 255.255.255.0push "route 192.168.122.0 255.255.255.0"keepalive 10 120cipher AES-256-CBCcompress lz4-v2push "compress lz4-v2"max-clients 2048user openvpngroup openvpnstatus /var/log/openvpn/openvpn-status.loglog-append /var/log/openvpn/openvpn.logverb 3mute 20EOFecho "添加防火墙"echo net.ipv4.ip_forward = 1 >> /etc/sysctl.confsysctl -pyum install iptables-services -ysystemctl disable --now firewalldsystemctl start iptablesiptables -Fiptables -t nat -A POSTROUTING -s 10.8.0.0/24 -j MASQUERADEiptables -vnL -t natmkdir -p /var/log/openvpnmkdir -p /etc/openvpn/certscp /etc/openvpn/easy-rsa-server/3/pki/issued/server.crt /etc/openvpn/certs/cp /etc/openvpn/easy-rsa-server/3/pki/private/server.key /etc/openvpn/certs/cp /etc/openvpn/easy-rsa-server/3/pki/ca.crt /etc/openvpn/certs/cp /etc/openvpn/easy-rsa-server/3/pki/dh.pem /etc/openvpn/certs/echo "重启OpenVpn"systemctl daemon-reloadsystemctl enable --now openvpn@serversystemctl restart openvpn@server服务端配置客户端的对应设置
#! /bin/bashread -p "请输入用户的姓名拼音(如:${NAME}): " NAMEread -p "请输入VPN服务端的公网IP(如:${IP}): " IPecho "客户端证书环境"cp -r /usr/share/easy-rsa/ /etc/openvpn/easy-rsa-clientcp /usr/share/doc/easy-rsa-3.0.8/vars.example /etc/openvpn/easy-rsa-client/3/varsacd /etc/openvpn/easy-rsa-client/3echo "初始化pki证书目录"# ./easyrsa init-pkiexpect << EOFspawn ./easyrsa init-pki expect { "removal" {send "yes\n"}}expect eofEOFecho "生成客户端证书"# ./easyrsa gen-req ${NAME} nopassexpect << EOFspawn ./easyrsa gen-req ${NAME} nopass expect { "${NAME}" {send "\n"}}expect eofEOFecho "将客户端证书同步到服务端"cd /etc/openvpn/easy-rsa-server/3./easyrsa import-req /etc/openvpn/easy-rsa-client/3/pki/reqs/${NAME}.req ${NAME}echo "查看客户端证书"ll pki/reqs/${NAME}.req /etc/openvpn/easy-rsa-client/3/pki/reqs/${NAME}.req echo "签发客户端证书,请输入:yes"# ./easyrsa sign client ${NAME}expect << EOFspawn ./easyrsa sign client ${NAME} expect { "*details" {send "yes\n"}}expect eofEOFecho "查看证书"cat pki/index.txtll pki/certs_by_serial/cat pki/issued/${NAME}.crt echo "创建客户端配置文件"mkdir -p /etc/openvpn/client/${NAME}cd /etc/openvpn/client/${NAME}cat > /etc/openvpn/client/${NAME}/client.conf <<EOFclientdev tunproto tcpremote ${IP} 1194resolv-retry infinitenobindca ca.crtcert ${NAME}.crtkey ${NAME}.keyremote-cert-tls servercipher AES-256-CBCverb 3compress lz4-v2EOFcp /etc/openvpn/easy-rsa-client/3/pki/private/${NAME}.key .cp /etc/openvpn/easy-rsa-server/3/pki/issued/${NAME}.crt .cp /etc/openvpn/easy-rsa-server/3/pki/ca.crt .echo "打包用户证书"tar -czvf ${NAME}.tar.gz ./#重启OpenVpnsystemctl daemon-reloadsystemctl enable --now openvpn@serversystemctl restart openvpn@server然后到客户端的配置,客户端的配置就比较简单了,步骤很少,就不用脚本了,给大家操作了解一下
epel源也是需要的
wget -O /etc/yum.repos.d/epel.repo https://mirrors.aliyun.com/repo/epel-7.repo然后下载openvpn
yum install openvpn -y将服务端打包好的认证文件拷贝过来,这里大家对应自己的ip来修改
scp 192.168.121.160:/etc/openvpn/client/yiyezhiqiu/yiyezhiqiu.tar.gz /etc/openvpn/解压认证包文件
tar -xf /etc/openvpn/yiyezhiqiu.tar.gz -C /etc/openvpn/然后就可以启动openven了
systemctl start openvpn@clientsystemctl enable openvpn@client查看启动日志一切正常
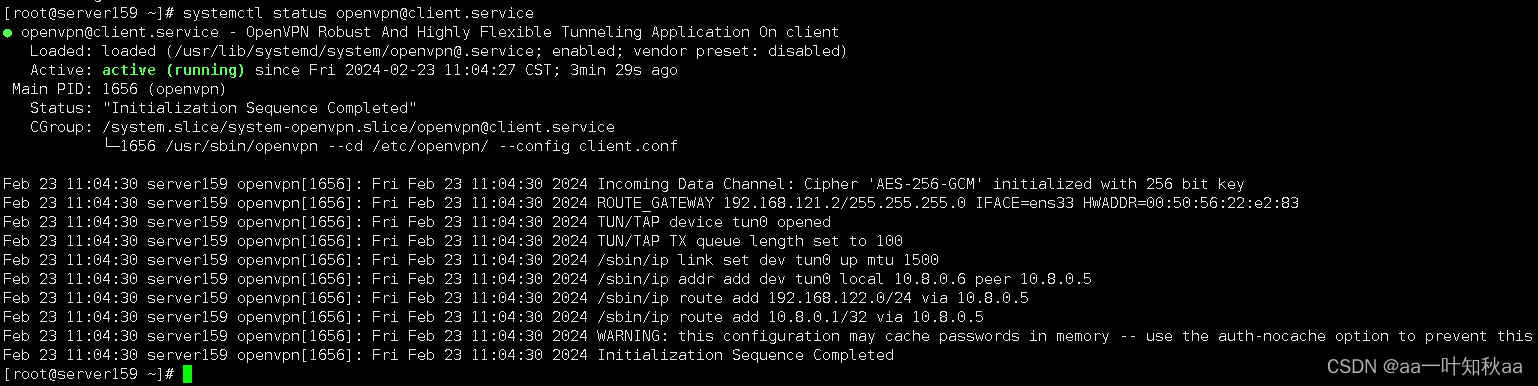
检测连接情况,ping没问题,ssh连接也可以
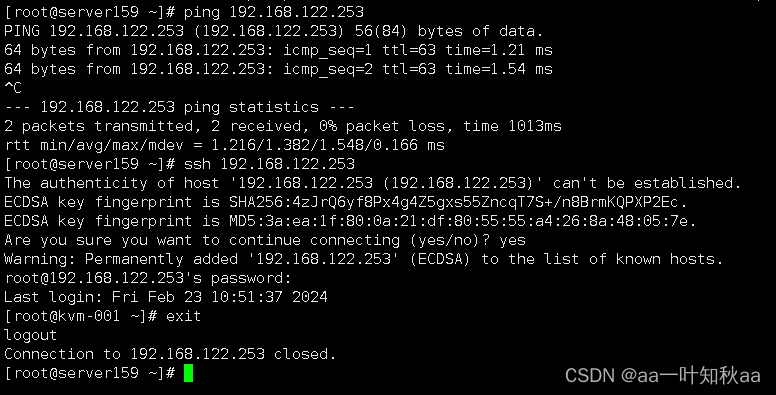 这样openvpn连接就可以了
这样openvpn连接就可以了